Hybrid cloud environments are becoming increasingly popular in the world of computing as they provide the best of both worlds by combining the scalability and cost-efficiency of public cloud services with the control and security of private clouds. However, hybrid cloud environments pose unique security challenges that require a different approach to traditional security solutions. In this article at Aods.info, we will explore some of the key security challenges associated with hybrid clouds, examine some of the best practices for securing hybrid cloud environments and some of the hybrid cloud security solutions.
Contents
- 1 Hybrid Cloud Security Definition
- 2 Security challenges in hybrid cloud environments
- 3 Best practices for securing hybrid cloud environments
- 4 What Are The Hybrid Cloud Security Solutions?
- 4.1 1. Cloud Access Security Broker (CASB)
- 4.2 2. Identity and Access Management (IAM)
- 4.3 3. Encryption
- 4.4 4. Security Information and Event Management (SIEM)
- 4.5 5. Virtual Private Networks (VPNs)
- 4.6 6. Security Orchestration, Automation, and Response (SOAR)
- 4.7 7. Data Loss Prevention (DLP)
- 4.8 8. Endpoint Protection
- 5 Conclusion
Hybrid Cloud Security Definition
Using workload mobility, data processing orchestration, and administration of IT systems that contain at least one private and one public cloud server, hybrid cloud security safeguards data, software applications, and IT infrastructure.
Based on compliance requirements, audits, regulations, and security, businesses distribute burden. With secured data containers, critical path processes can operate in a private cloud that is isolated from the public Internet. The sole means of communication between a private cloud and a public cloud is via encrypted application programming interfaces (APIs).
An organization can choose which workload processes go on the public cloud and which processes remain protected in the private cloud using a partitioned yet connected security strategy. This tactic aids in lowering the possibility of exposing sensitive data to cyberattacks and suffering significant harm from data breaches.
Security challenges in hybrid cloud environments
Hybrid cloud environments introduce unique security challenges that are not found in traditional on-premises or cloud-only environments. The following are some of the key security challenges in hybrid cloud environments:
- Data breaches: Hybrid cloud environments involve the movement of data between public and private clouds, which can increase the risk of data breaches. Data breaches can occur due to a variety of reasons, including insecure APIs, weak access controls, and misconfigured security settings.
- Compliance: Hybrid cloud environments need to comply with different regulations and industry standards, which can be challenging. For example, a company may need to comply with the General Data Protection Regulation (GDPR) in Europe, the Health Insurance Portability and Accountability Act (HIPAA) in the US, and the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada.
- Shadow IT: Hybrid cloud environments can increase the risk of shadow IT, which refers to the use of unauthorized cloud services by employees. Shadow IT can result in uncontrolled access to sensitive data, data breaches, and compliance violations.
- Complexity: Hybrid cloud environments are complex, which can make it challenging to manage security. IT teams need to manage security across multiple clouds, which can be difficult due to differences in security settings, access controls, and APIs.
- Lack of visibility: Hybrid cloud environments can lack visibility, which can make it difficult to detect and respond to security threats. IT teams need to have a complete view of their hybrid cloud environment to ensure that they can detect and respond to security threats in a timely manner.
Best practices for securing hybrid cloud environments
To address the security challenges associated with hybrid cloud environments, IT teams need to adopt a different approach to security. The following are some of the best practices for securing hybrid cloud environments:
- Adopt a zero-trust security model: A zero-trust security model involves treating all users and devices as untrusted, regardless of their location. This approach can help to reduce the risk of data breaches and ensure that sensitive data is protected.
- Use encryption: Encryption can help to protect data in transit and at rest. IT teams should ensure that all data is encrypted using strong encryption algorithms to reduce the risk of data breaches.
- Use identity and access management (IAM): IAM solutions can help to ensure that only authorized users have access to sensitive data. IT teams should implement IAM solutions that provide strong authentication and authorization controls to reduce the risk of unauthorized access.
- Monitor and log activity: IT teams should monitor and log activity in their hybrid cloud solutions to detect and respond to security threats. This can help to ensure that security incidents are detected and resolved in a timely manner.
- Regularly review and update security policies: IT teams should regularly review and update their security policies to ensure that they are up-to-date with the latest security threats and best practices. This can help to ensure that the hybrid cloud environment remains secure over time.
What Are The Hybrid Cloud Security Solutions?
There are several hybrid cloud security solutions that can help organizations secure their hybrid cloud environments. These solutions address different security challenges and can be used together to provide a comprehensive security posture. Here are some of the most common hybrid cloud security solutions:
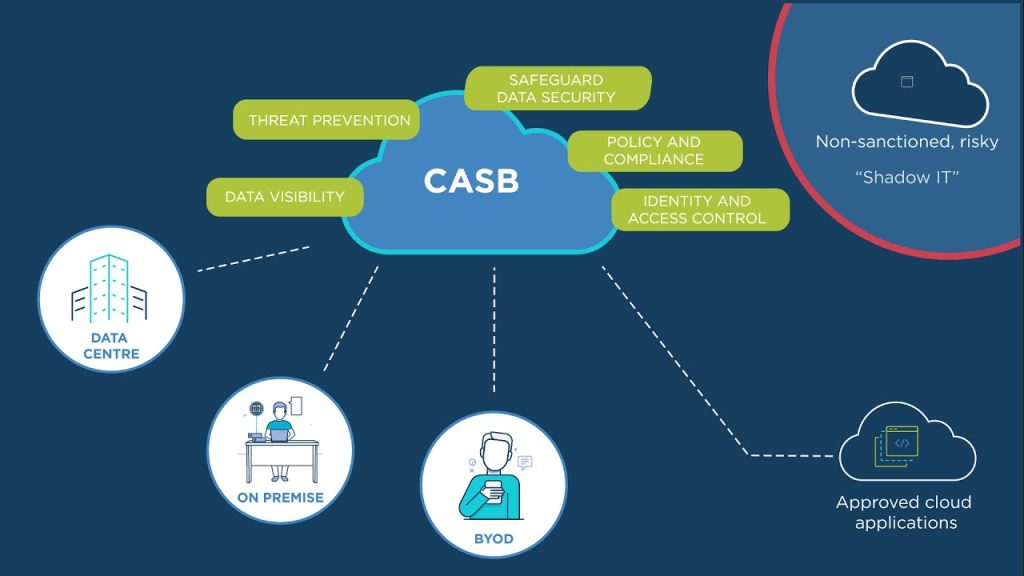
1. Cloud Access Security Broker (CASB)
A CASB is a security solution that provides visibility and control over cloud services used by an organization. CASBs can help organizations enforce security policies for accessing cloud services, monitor and prevent data leakage, and provide threat protection.
2. Identity and Access Management (IAM)
IAM hybrid cloud security solutions are used to manage user identities and access to resources. In hybrid cloud environments, IAM solutions can help to ensure that only authorized users have access to sensitive data and resources.
3. Encryption
Encryption can be used to protect data at rest and in transit. In hybrid cloud environments, encryption is particularly important when data is transferred between public and private clouds.
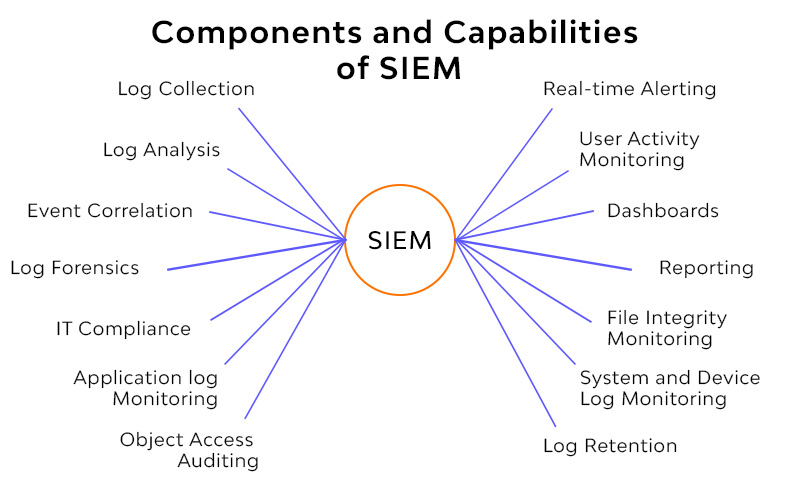
4. Security Information and Event Management (SIEM)
SIEM solutions can be used to collect and analyze security events from different sources in a hybrid cloud environment. This can help to detect and respond to security threats in a timely manner.
5. Virtual Private Networks (VPNs)
VPNs can be used to provide secure access to cloud resources over the internet. In hybrid cloud environments, VPNs can be used to establish secure connections between private and public clouds.
6. Security Orchestration, Automation, and Response (SOAR)
SOAR solutions can be used to automate security processes and response to security incidents. In hybrid cloud environments, SOAR can help to ensure that security incidents are detected and resolved quickly.
7. Data Loss Prevention (DLP)
DLP hybrid cloud security solutionscan be used to prevent sensitive data from leaving an organization. In hybrid cloud environments, DLP can be used to monitor and prevent data leakage to public clouds.
8. Endpoint Protection
Endpoint protection solutions can be used to protect endpoints in hybrid cloud environments. This can help to prevent malware infections and other security threats that can compromise sensitive data.
Conclusion
Hybrid cloud environments pose unique security challenges that require a different approach to security than traditional on-premises or cloud-only environments. Organizations need to adopt a comprehensive security posture that includes different security solutions that address different security challenges. It is important for organizations to evaluate their security needs and choose the hybrid cloud security solutions that best meet their requirements.